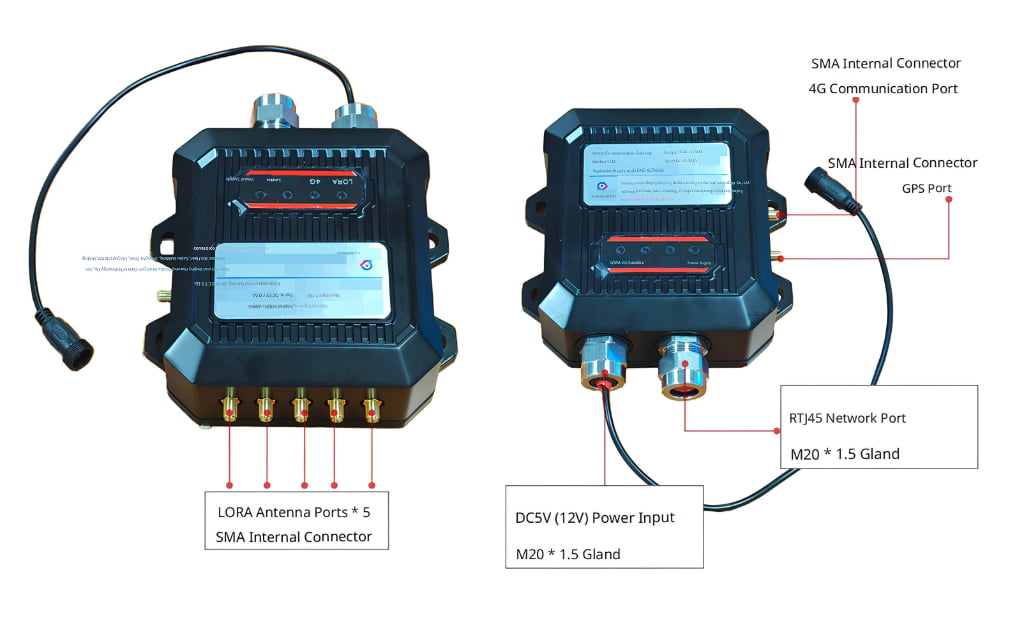
Communication Gateways
Communication gateways are a critical part of industrial RTLS and positioning systems, responsible for bridging field devices with local servers or cloud platforms when direct public network access is limited or unavailable.
GridRTLS provides industrial-grade communication gateways designed for reliable data transmission in harsh and complex environments such as chemical plants, factories, tunnels, mines, and large infrastructure sites.
Supplier / Manufacturer Overview
Built for SI / Engineering Teams
GridRTLS supplies industrial communication gateways that bridge UWB RTLS field devices with local servers or cloud platforms.
This category focuses on the data transmission layer—how positioning data leaves the site reliably, securely, and at scale.
FOCUS AREA
In real RTLS deployments, gateway reliability matters more than raw positioning accuracy.
Gateways determine whether data is delivered consistently across shifts, survives network interruptions,
and integrates cleanly with third-party positioning engines and customer platforms.
Our gateways are designed for industrial backhaul scenarios, supporting Ethernet,
private cellular (4G/5G), and local relay architectures where public network access may be limited or unavailable.
WHO WE WORK WITH
We primarily work with system integrators and engineering teams who already operate a positioning engine or RTLS platform
and need a stable, well-documented gateway layer to connect anchors, tags, and edge devices to their backend systems.
GATEWAY PORTFOLIO (WHAT YOU CAN EXPECT)
- Ethernet gateways for fixed industrial sites with existing wired infrastructure.
- Private cellular (4G/5G) gateways for remote sites, tunnels, mines, and temporary deployments.
- Local relay gateways for private networks and environments with restricted external connectivity.
- Industrial design expectations covering continuous operation, power stability, and predictable data throughput.
If you are selecting gateways for an RTLS project, this page is intended to help you
define communication architecture, backhaul options, and RFQ inputs,
and move toward an RFQ-ready gateway BOM without re-quoting later.
Capability highlights
Designed for continuous operation in factories, tunnels, and outdoor sites where consumer networking equipment is not suitable.
Support Ethernet, private cellular (4G/5G), and local relay models to match site constraints and IT policies.
Gateways focus on data forwarding and protocol handling, leaving positioning logic to the customer’s RTLS engine or platform.
Consistent configuration and provisioning support pilot → rollout without gateway behavior changes between batches.
Clear integration notes, network requirements, and commissioning expectations for SI teams.
Selection criteria (what to specify in an RFQ)
1
Backhaul method
⌄
Ethernet, private cellular (4G/5G), or local relay. This defines hardware, SIM strategy, and network policy alignment.
2
Expected data throughput
⌄
Number of anchors/tags per gateway and refresh rate determine throughput and buffering requirements.
3
Network availability & stability
⌄
Define whether gateways must tolerate intermittent connectivity and how data buffering/retry should behave.
4
Integration interface
⌄
Specify expected data format, protocol, and whether data is forwarded raw or pre-processed.
5
Power & installation constraints
⌄
Power source, mounting method, and environmental exposure (temperature, dust, vibration).
6
Security & IT policy
⌄
Firewall rules, private APN usage, VPN requirements, or on-premise routing constraints.
7
Deployment scale & batch consistency
⌄
Pilot size vs rollout size affects provisioning workflow and revision control expectations.
Customization / OEM / ODM
For communication gateways, customization typically focuses on network configuration,
enclosure options, and deployment-specific parameters rather than core functionality.
We recommend keeping gateway logic stable and aligning customization with IT and security policies early.
OEM/ODM scope may include branding, enclosure adjustments, power options, and controlled firmware parameters.
Deeper customization affecting protocols or security models should be confirmed early,
as it impacts validation and long-term maintainability.
Logo, asset labels, packaging.
APN settings, static routing, VPN parameters.
DIN-rail mounting, extended temperature enclosure.
SIM strategy, carrier selection, private network alignment.
Firewall rules, certificate handling, IT validation workflow.
Pre-configured gateways for large rollouts.
Integration & architecture
Communication gateways sit between field devices and the customer platform.
From an integration perspective, they should be treated as data transport and routing components,
not positioning logic nodes.
- Confirm how raw data or event streams are forwarded to your RTLS engine.
- Define buffering and retry behavior for unstable networks.
- Align gateway security settings with customer IT policies before deployment.
- Plan provisioning and monitoring processes for multi-gateway rollouts.
Related solutions
Common solution patterns where this category is typically used.
Related industries
Where this category is most commonly deployed.
Factory, delivery discipline & real deployments
Evidence that matters to SI teams: how we lock BOMs, keep batch consistency, and ship integration-ready hardware.
Read full supplier proof ⌄
We align network role, backhaul method (Ethernet / private cellular / local relay),
and data forwarding expectations before locking the shipment configuration.
This prevents re-configuration and re-validation during site deployment.
We keep firmware parameters, network behavior, and interface expectations consistent
across pilot and rollout batches, so SI teams do not face
“same model, different behavior” issues during expansion.
- We supply gateway hardware and integration-ready documentation.
- We do not operate or maintain the customer’s RTLS platform or cloud services.
- Site delivery, IT policy enforcement, and platform integration are handled by system integrators or project owners.
- Hardware + integration-ready documentation supplied; no on-site cabling / civil construction.
- No turnkey RTLS platform operation for end customers; platform & site delivery handled by SI / partners.
pcat_factory_photos to show real installation proof.
Gateway deployment may require alignment with customer IT and security policies
(firewall rules, private APN, VPN, or routing constraints).
These requirements should be defined before shipment.
Warranty coverage and RMA handling follow agreed procurement terms.
Clear batch identification and configuration records support efficient troubleshooting and replacement.
-
Network connectivity verification
Each gateway is verified for basic network functionality based on its intended backhaul
(Ethernet or cellular), including link establishment and recovery after interruption. -
Throughput and buffering validation
Gateways are checked for stable data forwarding under expected device load,
including basic buffering behavior when network availability is temporarily limited. -
Power stability and long-run testing
Power input behavior and continuous operation are verified to reduce the risk of
unexpected resets or instability during long-term site operation.
FAQ
What is the role of a communication gateway in an RTLS system? ⌄
The gateway is responsible for data transport, not positioning logic.
It bridges field devices (anchors, tags, terminals) with the customer’s local server or cloud platform.
Position calculation, business rules, and visualization are typically handled by the RTLS engine, not the gateway.
How do I choose between Ethernet and cellular (4G/5G) gateways? ⌄
Use Ethernet gateways when stable wired infrastructure is available on site.
Cellular gateways are more suitable for tunnels, mines, temporary sites, or locations with limited IT access.
The choice affects power design, SIM strategy, security policy, and long-term operating cost.
Do gateways perform any positioning or data processing? ⌄
No. Gateways focus on data forwarding and basic protocol handling.
They do not perform UWB positioning calculations or application-level logic.
This separation keeps the system architecture flexible and easier to maintain.
What should be specified in an RFQ for communication gateways? ⌄
Key RFQ inputs include backhaul method (Ethernet / 4G / 5G / local relay),
expected device count and data rate, network availability assumptions,
security or IT policy constraints, and deployment scale (pilot vs rollout).
How does gateway selection affect system scalability? ⌄
Gateway capacity, buffering behavior, and provisioning workflow directly affect scalability.
Defining these parameters early helps ensure that pilot configurations can be reused
without redesign when moving to multi-site or large-scale deployment.
How do gateways handle unstable or intermittent networks? ⌄
Gateways are typically configured to tolerate temporary network interruptions,
with basic buffering and retry behavior.
Exact behavior depends on configuration and should be aligned with the customer platform
during the integration phase.
Are communication gateways tied to a specific RTLS platform? ⌄
No. Gateways are designed to integrate with third-party RTLS engines and platforms.
Integration is based on agreed data formats, protocols, and routing rules,
allowing SI teams to keep control of platform choice.
What security or IT considerations should be addressed? ⌄
Typical considerations include firewall rules, private APN usage for cellular gateways,
VPN requirements, and routing policies.
These should be defined before shipment to avoid site delays or reconfiguration.
How is batch consistency ensured across multiple gateway shipments? ⌄
Gateway configuration, firmware parameters, and labeling are kept consistent across batches.
This helps SI teams deploy additional gateways without unexpected behavior differences
between pilot and rollout phases.

Planning RTLS communication gateways? Get an RFQ-ready backhaul architecture.<br />
Define gateway role, backhaul method (Ethernet / 4G/5G / relay), throughput, and security requirements<br /> before RFQ. This helps SI teams lock communication architecture early and avoid re-quoting later.<br />
Ready to Deploy RTLS?
Share your site layout and accuracy needs--we'll suggest a practical setup.
